Passwords Passphrases And Pins Are Examples Of Which Security Term
News Leon
Mar 31, 2025 · 6 min read
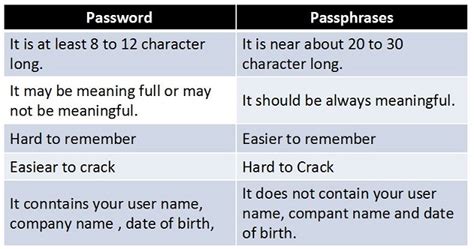
Table of Contents
Passwords, Passphrases, and PINs: Understanding Authentication Factors and Strengthening Your Digital Security
Passwords, passphrases, and PINs are all examples of authentication factors, specifically focusing on something you know. They are fundamental components of a broader security strategy aimed at verifying your identity and protecting your sensitive information in the digital world. Understanding their nuances, strengths, and weaknesses is crucial for establishing a robust security posture. This article will delve into the specifics of these authentication methods, explore their role within the larger security landscape, and provide practical advice on choosing and managing them effectively.
What is Authentication?
Before diving into passwords, passphrases, and PINs, let's establish a clear understanding of authentication. Authentication is the process of verifying the identity of a user, device, or other entity attempting to access a system or resource. It confirms: "Are you who you say you are?" This is different from authorization, which determines what a verified user is permitted to do once authenticated. Authentication is the first gatekeeper, and it's critical for maintaining security.
Several factors are used in authentication, categorized as:
- Something you know: Passwords, passphrases, PINs, security questions.
- Something you have: Smart cards, security tokens, mobile devices with authentication apps.
- Something you are: Biometrics like fingerprints, facial recognition, iris scans.
- Somewhere you are: Geolocation data, IP address verification.
Deep Dive into Passwords, Passphrases, and PINs
While all three – passwords, passphrases, and PINs – fall under the "something you know" category, they differ significantly in their characteristics and security implications.
Passwords: The Foundation of Digital Security (But Often Weak)
A password is a secret word or phrase used to verify the identity of a user. It's the most widely used authentication method, but also often the weakest link in security chains. Weak passwords are easily guessed or cracked using brute-force attacks or dictionary attacks.
Characteristics of Passwords:
- Typically shorter: Often limited in length by system requirements.
- Character restrictions: May restrict the use of special characters or uppercase letters.
- Vulnerable to guessing: Easily compromised if chosen poorly.
- Susceptible to brute-force attacks: Computers can try numerous combinations rapidly.
- Prone to reuse: Users often reuse the same password across multiple accounts.
Improving Password Security:
- Use strong passwords: Include a mix of uppercase and lowercase letters, numbers, and symbols. Aim for at least 12 characters.
- Use a unique password for each account: Avoid reusing passwords across different websites and services. A breach on one site shouldn't compromise all your accounts.
- Utilize a password manager: These tools generate strong, unique passwords and securely store them, eliminating the need to remember everything.
- Enable multi-factor authentication (MFA): Adding a second layer of security, such as a code from your phone, significantly improves protection even if a password is compromised.
- Regularly update passwords: Change passwords periodically, especially for sensitive accounts.
Passphrases: The Stronger Alternative
A passphrase is a longer, more complex sequence of words, often forming a sentence or phrase that is easier to remember than a randomly generated password. Because they are longer and more complex, passphrases offer superior resistance to brute-force attacks.
Advantages of Passphrases:
- Easier to remember: Meaningful phrases are simpler to memorize than random character strings.
- More resistant to brute-force attacks: The longer length significantly increases the time it would take to crack them.
- Improved security: A well-chosen passphrase is far stronger than a typical password.
Creating Strong Passphrases:
- Use a memorable phrase: Base the passphrase on something you already know, like a favorite quote or a line from a song.
- Add extra layers of complexity: Include numbers, symbols, or unusual capitalization to make it even more secure.
- Avoid clichés or common phrases: Don't use anything easily guessable.
PINs: Short and Sweet, But Risky
A PIN (Personal Identification Number) is a short numerical code used for authentication, often used for accessing bank accounts, credit cards, or mobile devices. PINs are typically shorter than passwords or passphrases, making them more vulnerable to brute-force attacks and easier to guess.
Limitations of PINs:
- Short length: Typically 4 to 6 digits, limiting the number of possible combinations.
- Vulnerable to shoulder surfing: Easily observed by someone watching you type.
- Susceptible to brute-force attacks: Shorter length makes them easier to crack.
- Limited character set: Only numbers, reducing complexity.
Improving PIN Security:
- Use a complex PIN: Choose a PIN that's difficult to guess, avoiding obvious sequences like birthdays or anniversaries.
- Be mindful of your surroundings: Avoid using your PIN in public places where others can see you.
- Use a different PIN for each account: Don't reuse the same PIN for multiple services.
The Role of Authentication Factors in a Broader Security Strategy
Passwords, passphrases, and PINs are just one piece of the puzzle when it comes to digital security. A robust security strategy should incorporate multiple layers of protection, utilizing a variety of authentication factors. This is where multi-factor authentication (MFA) comes into play. MFA requires users to provide multiple pieces of evidence to verify their identity, significantly enhancing security. For instance, MFA might require a password (something you know) and a verification code sent to your phone (something you have).
The combination of factors makes it exponentially more difficult for unauthorized individuals to gain access, even if one factor is compromised. Employing MFA is a crucial step in protecting your accounts and data from cyber threats.
Best Practices for Password, Passphrase, and PIN Management
- Choose strong and unique credentials: This is paramount for all three types of authentication.
- Use a password manager: Streamline password management and ensure strong, unique credentials for each account.
- Enable MFA wherever possible: Add that extra layer of security to protect your accounts.
- Keep your devices secure: Install anti-virus software, keep your operating system updated, and be wary of phishing scams and malware.
- Educate yourself on security best practices: Stay informed about the latest threats and techniques for staying safe online.
- Report suspicious activity immediately: If you suspect your accounts have been compromised, take action swiftly to mitigate the damage.
The Future of Authentication: Beyond Passwords
While passwords, passphrases, and PINs remain widely used, the security landscape is constantly evolving. The limitations of relying solely on "something you know" are increasingly apparent. The future of authentication is likely to move towards more robust methods, including:
- Passwordless authentication: Eliminating the need for passwords altogether by using biometrics or other methods.
- Behavioral biometrics: Analyzing user behavior patterns to verify identity.
- Enhanced MFA methods: Combining multiple factors in more sophisticated ways.
Conclusion: Strengthening Your Digital Defenses
Passwords, passphrases, and PINs are essential elements of digital security, serving as the initial gatekeepers to your online accounts and information. Understanding their strengths and weaknesses, employing best practices, and adopting a multi-layered security strategy are crucial for safeguarding your personal data in today's increasingly complex digital environment. By embracing stronger authentication methods and staying informed about evolving security threats, you can significantly reduce your risk and strengthen your digital defenses. Remember, vigilance and proactive security measures are your best allies in the ongoing battle against cyber threats.
Latest Posts
Latest Posts
-
Adjacent Angles Whose Sum In 180 Degrees
Apr 01, 2025
-
Lewis Dot Structure For Magnesium Chloride
Apr 01, 2025
-
A Group Of Related Records Is Called A Table
Apr 01, 2025
-
Provides Long Term Energy Storage For Animals
Apr 01, 2025
-
The Average Propensity To Consume Refers To
Apr 01, 2025
Related Post
Thank you for visiting our website which covers about Passwords Passphrases And Pins Are Examples Of Which Security Term . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
